这篇文章给大家介绍Burpsuite插件burpFakeIP怎么用,内容非常详细,感兴趣的小伙伴们可以参考借鉴,希望对大家能有所帮助。
今天给大家介绍一款Burpsuite插件,burpFakeIP
一、下载地址
https://github.com/TheKingOfDuck/burpFakeIP
二、安装插件
1、解压到本地
2、打开burpsuite,选择Extender,Add
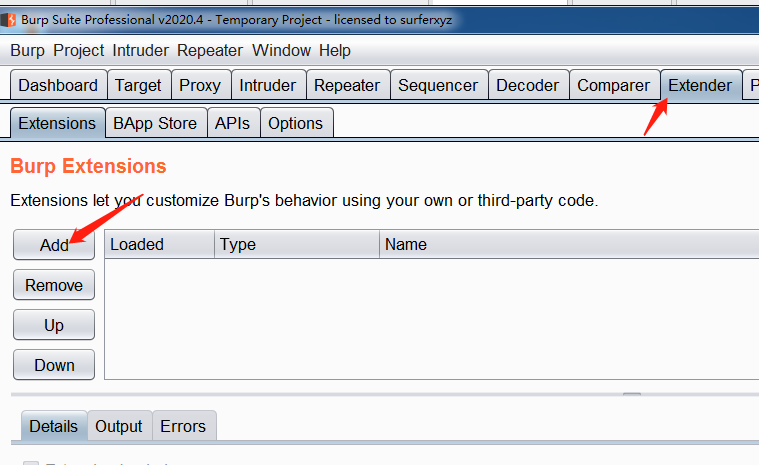
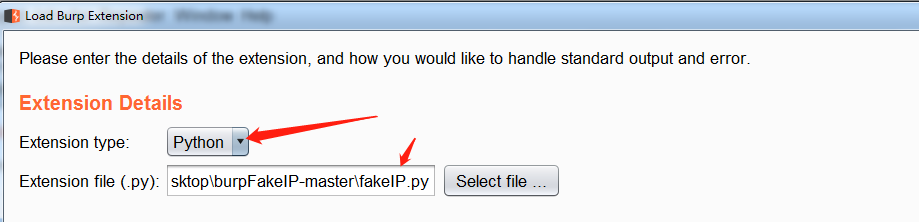
3、选择下载好python插件,选择下一步
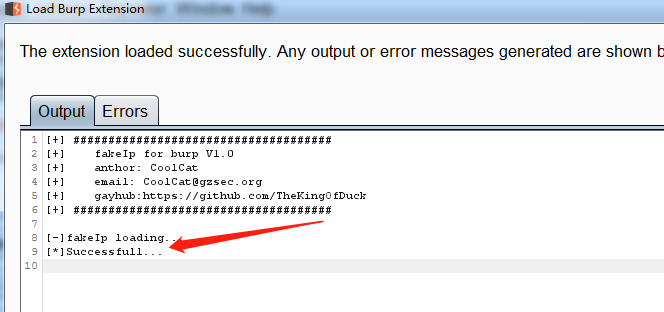
4、安装成功
三、使用方法
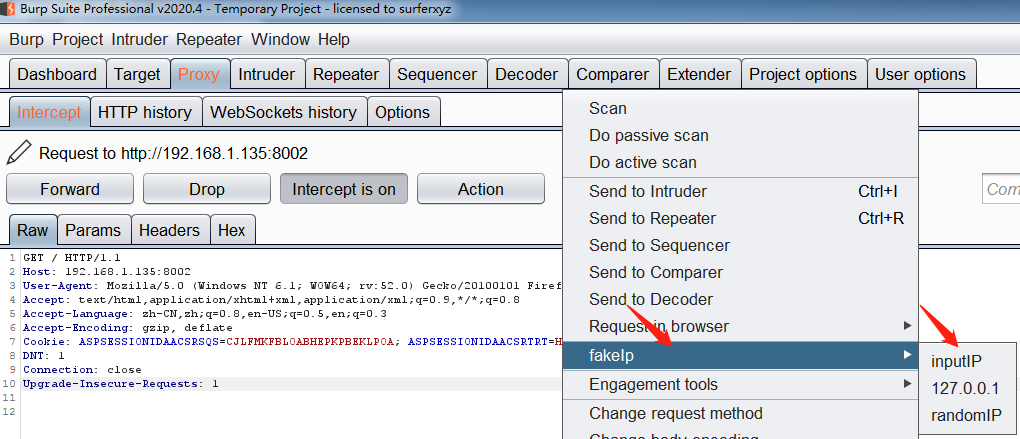
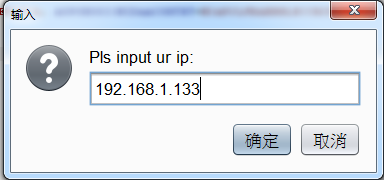
1、伪造指定ip,右击抓到的数据包,选择fakeip,inputIP,输入想要用的ip地址,点击确定,自动添加
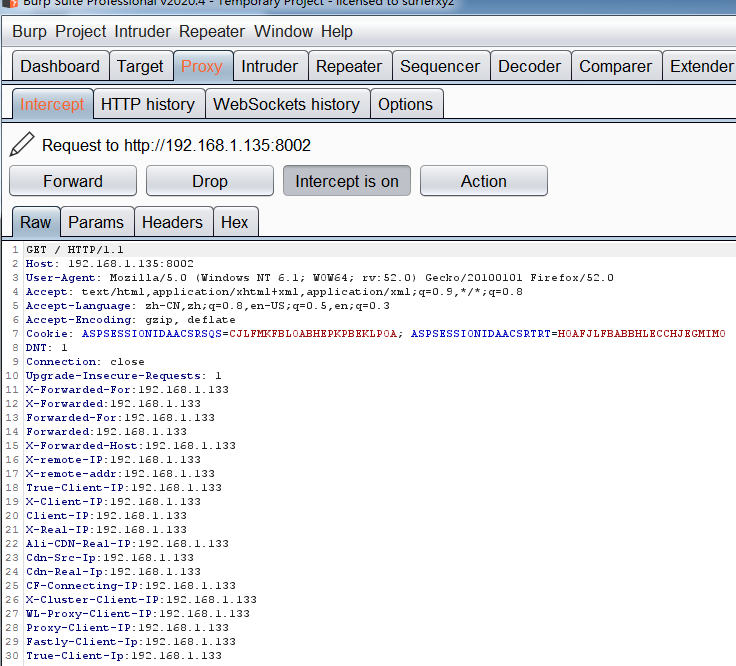
2、伪造本地ip,右击数据包选择127.0.0.1,自动生成如下数据包
GET / HTTP/1.1Host: 192.168.1.135:8002User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateCookie: ASPSESSIONIDAACSRSQS=CJLFMKFBLOABHEPKPBEKLPOA; ASPSESSIONIDAACSRTRT=HOAFJLFBABBHLECCHJEGMIMODNT: 1Connection: closeUpgrade-Insecure-Requests: 1X-Forwarded-For:127.0.0.1X-Forwarded:127.0.0.1Forwarded-For:127.0.0.1Forwarded:127.0.0.1X-Forwarded-Host:127.0.0.1X-remote-IP:127.0.0.1X-remote-addr:127.0.0.1True-Client-IP:127.0.0.1X-Client-IP:127.0.0.1Client-IP:127.0.0.1X-Real-IP:127.0.0.1Ali-CDN-Real-IP:127.0.0.1Cdn-Src-Ip:127.0.0.1Cdn-Real-Ip:127.0.0.1CF-Connecting-IP:127.0.0.1X-Cluster-Client-IP:127.0.0.1WL-Proxy-Client-IP:127.0.0.1Proxy-Client-IP:127.0.0.1Fastly-Client-Ip:127.0.0.1True-Client-Ip:127.0.0.1
3、伪造随机IP,右击数据包选择randomIP,生成如下数据包
GET / HTTP/1.1Host: 192.168.1.135:8002User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateCookie: ASPSESSIONIDAACSRSQS=CJLFMKFBLOABHEPKPBEKLPOA; ASPSESSIONIDAACSRTRT=HOAFJLFBABBHLECCHJEGMIMODNT: 1Connection: closeUpgrade-Insecure-Requests: 1X-Forwarded-For:37.120.247.234X-Forwarded:37.120.247.234Forwarded-For:37.120.247.234Forwarded:37.120.247.234X-Forwarded-Host:37.120.247.234X-remote-IP:37.120.247.234X-remote-addr:37.120.247.234True-Client-IP:37.120.247.234X-Client-IP:37.120.247.234Client-IP:37.120.247.234X-Real-IP:37.120.247.234Ali-CDN-Real-IP:37.120.247.234Cdn-Src-Ip:37.120.247.234Cdn-Real-Ip:37.120.247.234CF-Connecting-IP:37.120.247.234X-Cluster-Client-IP:37.120.247.234WL-Proxy-Client-IP:37.120.247.234Proxy-Client-IP:37.120.247.234Fastly-Client-Ip:37.120.247.234True-Client-Ip:37.120.247.234
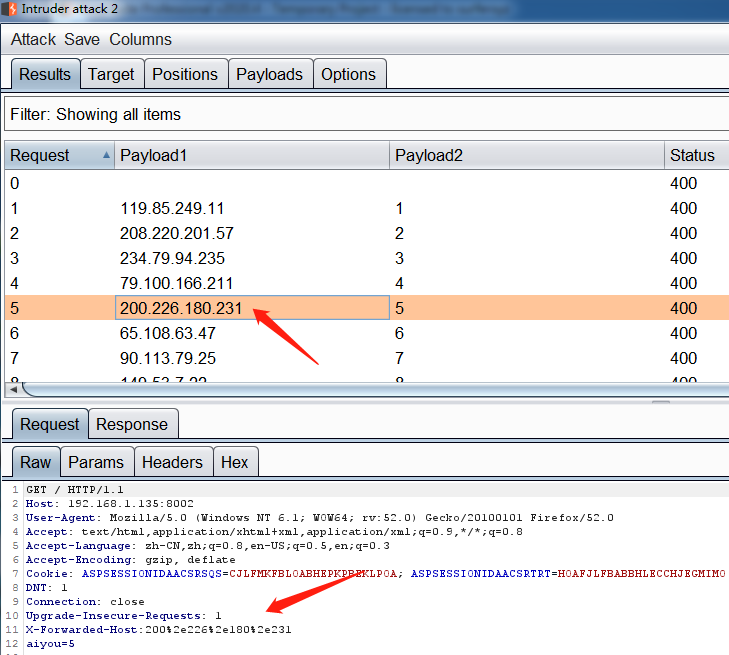
4、随机ip爆破,伪造随机ip爆破是本插件最核心的功能。
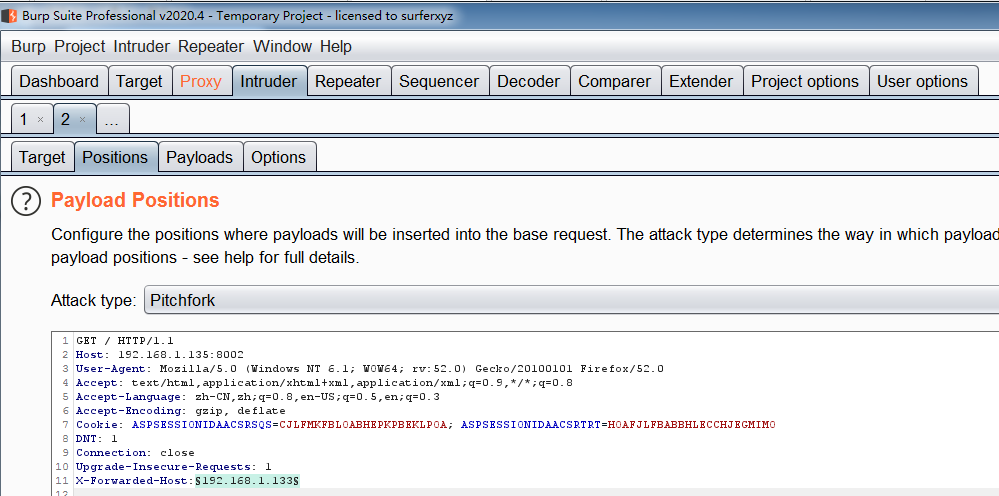
将数据包发送到Intruder模块,在Positions中切换Attack type为Pitchfork模式,选择好有效的伪造字段,以及需要爆破的字段
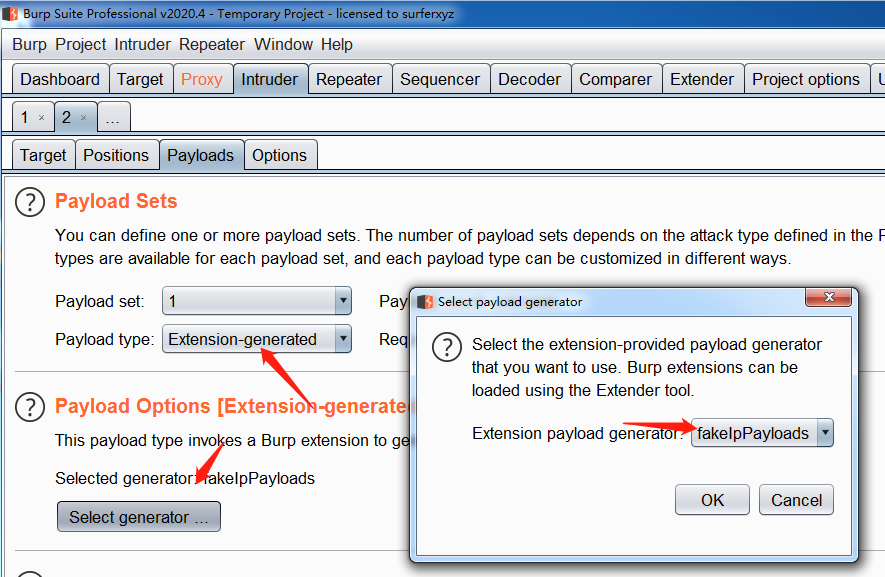
将Payload来源设置为Extensin-generated,并设置负载伪fakeIpPayloads,然后设置第二个变量。
点击Start attack开始爆破.
关于Burpsuite插件burpFakeIP怎么用就分享到这里了,希望以上内容可以对大家有一定的帮助,可以学到更多知识。如果觉得文章不错,可以把它分享出去让更多的人看到。
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。