Sentry是一个RPC服务,将认证元数据信息存储在关系型数据库,并提供RPC接口检索和操作权限。利用Kerveros支持安全访问。Sentry Service通过后台数据库存储提供认证元数据信息,不处理真实的权限验证,当Hive,Impala等服务的配置使用Sentry权限的时候,Hive,Impala只作为Sentry的client。
最早的Sentry是使用policy file配置权限,逐渐版本升级过程中,目前采用关系型数据库存储权限角色等。使用新的Sentry服务相比于旧的policy file能够更容易处理用户权限,新的Sentry服务提供了更传统的 GRANT/REVOKE语句修改权限。
早版本Sentry中的策略文件policy file:
[groups]
manager = customers_insert_role,
customers_select_role
analyst = customers_select_role
[roles]
customers_insert_role = server=server1->db=customers->table=*->action=insert
customers_select_role = server=server1->db=customers->table=*->action=selectSentry历史版本功能:
Sentry with policy files is added in CDH 5.1.0.
Sentry with config support is added in CDH 5.5.0.
Sentry with database-backed Sentry service is added with CDH 5.8.0.
Sentry中基础名词:
1.object Sentry认证规则所保护的一个对象,包括 server, database, table, URI, collection, and config
2.role 访问给定object的规则集合
3.privilege 包括insert select update等
4.user 来自于能够访问Sentry服务的一个认证系统用户,user可以是Kerberos的principal, LDAP的userid,或其他认证系统的标识
5.group 组,一个或者多个用户的集合,Sentry中将role分配给group,一个组就相应担当某个角色
6.A configured group provider determines a user’s affiliation with a group. The current release supports HDFS-backed groups and locally configured groups.
| Privilege | Object |
| INSERT | DB, TABLE |
| SELECT | SERVER, DB, TABLE, COLUMN |
| UPDATE | COLLECTION, CONFIG |
| QUERY | COLLECTION, CONFIG |
| ALL | SERVER, TABLE, DB, URI, COLLECTION, CONFIG |
Sentry权限模型:
Sentry使用基于角色权限模型,有如下特征
1、允许所有用户执行show functions,show locks等
2、允许用户看到那些有权限的tables,databases,collections,configs等
3、HiveQL执行例如LOAD,IMPORT等操作,需要用户有相应URI的权限
4、赋予一个URI某个权限,其子目录也递归赋予这个权限,所以只需将权限grant给一个父目录
5、CDH 5.5引入Column级别的访问控制,之前版本的如果要控制到列级别访问,使用View,创建一个只包含有访问权限Column的View
Tips
Hive中使用Sentry的时候,必须使用Beeline方式执行查询,Hive Cli方式不支持Sentry
Hive On Sentry中Object层级结构关系
权限能够赋予层级中的不同的object,一个权限如果赋予层级中一个object,则这个object子层级中的object继承这个权限。
比如赋予DATABASE的SELECT权限给用户A,则用户A拥有DATABASE下所有Object的SELECT权限
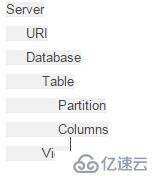
权限类型和Object的对应关系
| Privilege | Object |
| INSERT | DB, TABLE |
| SELECT | DB, TABLE, VIEW, COLUMN |
| ALL | SERVER, TABLE, DB, URI |
权限层级
| Base Object | Granular privileges on object | Container object that contains the base object | Privileges on container object that implies privileges on the base object |
| DATABASE | ALL | SERVER | ALL |
| TABLE | INSERT | DATABASE | ALL |
| TABLE | SELECT | DATABASE | ALL |
| COLUMN | SELECT | DATABASE | ALL |
| VIEW | SELECT | DATABASE | ALL |
Hive&Impala操作权限表
| Operation | Scope | Privileges Required | URI |
| CREATE DATABASE | SERVER | ALL | |
| DROP DATABASE | DATABASE | ALL | |
| CREATE TABLE | DATABASE | ALL | |
| DROP TABLE | TABLE | ALL | |
| CREATE VIEW-This operation is allowed if you have column-level SELECTaccess to the columns being used. | DATABASE; SELECT on TABLE; | ALL | |
| ALTER VIEW-This operation is allowed if you have column-level SELECTaccess to the columns being used. | VIEW/TABLE | ALL | |
| DROP VIEW | VIEW/TABLE | ALL | |
| ALTER TABLE .. ADD COLUMNS | TABLE | ALL | |
| ALTER TABLE .. REPLACE COLUMNS | TABLE | ALL | |
| ALTER TABLE .. CHANGE column | TABLE | ALL | |
| ALTER TABLE .. RENAME | TABLE | ALL | |
| ALTER TABLE .. SET TBLPROPERTIES | TABLE | ALL | |
| ALTER TABLE .. SET FILEFORMAT | TABLE | ALL | |
| ALTER TABLE .. SET LOCATION | TABLE | ALL | URI |
| ALTER TABLE .. ADD PARTITION | TABLE | ALL | |
| ALTER TABLE .. ADD PARTITION location | TABLE | ALL | URI |
| ALTER TABLE .. DROP PARTITION | TABLE | ALL | |
| ALTER TABLE .. PARTITION SET FILEFORMAT | TABLE | ALL | |
| SHOW CREATE TABLE | TABLE | SELECT/INSERT | |
| SHOW PARTITIONS | TABLE | SELECT/INSERT | |
| SHOW TABLES-Output includes all the tables for which the user has table-level privileges and all the tables for which the user has some column-level privileges. | TABLE | SELECT/INSERT | |
| SHOW GRANT ROLE-Output includes an additional field for any column-level privileges. | TABLE | SELECT/INSERT | |
| DESCRIBE TABLE-Output shows all columns if the user has table level-privileges or SELECT privilege on at least one table column | TABLE | SELECT/INSERT | |
| LOAD DATA | TABLE | INSERT | URI |
| SELECT-You can grant the SELECT privilege on a view to give users access to specific columns of a table they do not otherwise have access to. -See Column-level Authorization for details on allowed column-level operations. | VIEW/TABLE; COLUMN | SELECT | |
| INSERT OVERWRITE TABLE | TABLE | INSERT | |
| CREATE TABLE .. AS SELECT-This operation is allowed if you have column-level SELECTaccess to the columns being used. | DATABASE; SELECT on TABLE | ALL | |
| USE <dbName> | Any | ||
| CREATE FUNCTION | SERVER | ALL | |
| ALTER TABLE .. SET SERDEPROPERTIES | TABLE | ALL | |
| ALTER TABLE .. PARTITION SET SERDEPROPERTIES | TABLE | ALL | |
| Hive-Only Operations | |||
| INSERT OVERWRITE DIRECTORY | TABLE | INSERT | URI |
| Analyze TABLE | TABLE | SELECT + INSERT | |
| IMPORT TABLE | DATABASE | ALL | URI |
| EXPORT TABLE | TABLE | SELECT | URI |
| ALTER TABLE TOUCH | TABLE | ALL | |
| ALTER TABLE TOUCH PARTITION | TABLE | ALL | |
| ALTER TABLE .. CLUSTERED BY SORTED BY | TABLE | ALL | |
| ALTER TABLE .. ENABLE/DISABLE | TABLE | ALL | |
| ALTER TABLE .. PARTITION ENABLE/DISABLE | TABLE | ALL | |
| ALTER TABLE .. PARTITION.. RENAME TO PARTITION | TABLE | ALL | |
| MSCK REPAIR TABLE | TABLE | ALL | |
| ALTER DATABASE | DATABASE | ALL | |
| DESCRIBE DATABASE | DATABASE | SELECT/INSERT | |
| SHOW COLUMNS-Output for this operation filters columns to which the user does not have explicit SELECT access | TABLE | SELECT/INSERT | |
| CREATE INDEX | TABLE | ALL | |
| DROP INDEX | TABLE | ALL | |
| SHOW INDEXES | TABLE | SELECT/INSERT | |
| GRANT PRIVILEGE | Allowed only for Sentry admin users | ||
| REVOKE PRIVILEGE | Allowed only for Sentry admin users | ||
| SHOW GRANT | Allowed only for Sentry admin users | ||
| SHOW TBLPROPERTIES | TABLE | SELECT/INSERT | |
| DESCRIBE TABLE .. PARTITION | TABLE | SELECT/INSERT | |
| ADD JAR | Not Allowed | ||
| ADD FILE | Not Allowed | ||
| DFS | Not Allowed | ||
| Impala-Only Operations | |||
| EXPLAIN | TABLE; COLUMN | SELECT | |
| INVALIDATE METADATA | SERVER | ALL | |
| INVALIDATE METADATA <table name> | TABLE | SELECT/INSERT | |
| REFRESH <table name> or REFRESH <table name> PARTITION (<partition_spec>) | TABLE | SELECT/INSERT | |
| DROP FUNCTION | SERVER | ALL | |
| COMPUTE STATS | TABLE | ALL | |
通过HUE管理Sentry:http://10120275.blog.51cto.com/10110275/1956777
亿速云「云服务器」,即开即用、新一代英特尔至强铂金CPU、三副本存储NVMe SSD云盘,价格低至29元/月。点击查看>>
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。