最近尝试了解了一下微软新一代的×××技术DirectAccess(其实也不新了,从WIN2K8R2就开始有了),看了一些资料,现在自己写点总结来加强理解和记忆。如果有写错了的话,欢迎指正!
**********************
DirectAcces工作过程中会先后经历两个与内网建立联系的阶段。第一阶段是和内网DNS、DC建立联系。第二阶段才是和要访问的内网资源建立联系。DirectAccess与其他×××解决方案的关键区别在于:
1. 只要客户端连接了互联网,它就会自动发起与内网DNS、DC的联系,从而使系统管理员可以随时管理在外漫游的客户端。一个典型的应用场景是,漫游客户端只要连上互联网,就可以获得内网推过去的GPO,补丁等。
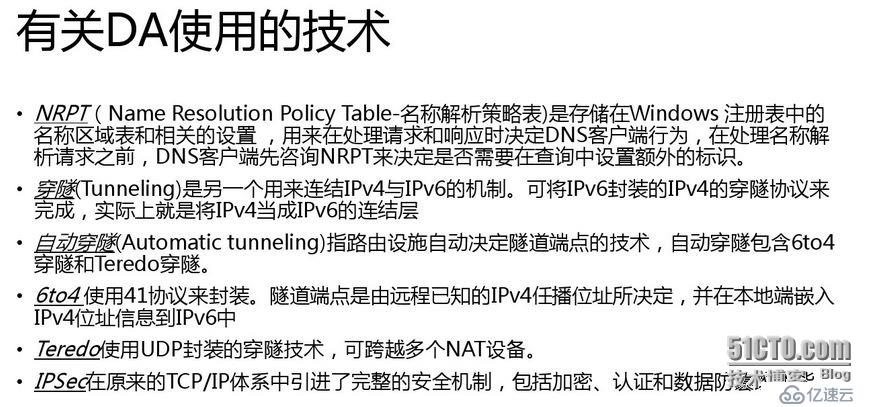
2. 采用Name Resolution Policy Table(名称解析策略表)技术,实现内网与互联网流量访问的分离。
回到区别1,,如何才能自动发起与内网DNS、DC的联系呢?首先需要一个发现机制。为此,这里引入了Network Location Server的概念。NLS是企业内网中的一台Web服务器。客户端首先尝试与NLS取得联系,如果能取得联系,说明DirectAccess已经在工作。如果不能与NLS取得联系,那么开始进入两个阶段的与内网建立联系的工作过程。也就是说,NLS的作用体现在下图步骤中的第2步。
发现机制之后,才开始了两个阶段的与内网建立联系的过程。建立联系的过程涉及到:建立流量通道,身份验证。第一阶段的验证对象是客户端计算机,需要内网的PKI架构实现对客户端发放证书。第二阶段的验证是对客户端计算机和用户的双重验证,除了验证计算机证书,还要认证域用户的凭据(也就是域用户登录时的那一套验证)。
PS: 以下图片截取自http://wenku.baidu.com/view/108a09e704a1b0717fd5dd85
PS2: 网上找了前人做的实验《如何在企业内部构建Direct Access环境》http://wenku.baidu.com/link?url=jqQ_xzlSAT9I5zoJ_OFjOqN_gGAVSrSY68ItRzKvICceQLpLbewgaXeTrEzNyjnNIUksLiBj_xPzXFtQN6pIyrB2Ov5wc-RQykD16PKjdLW
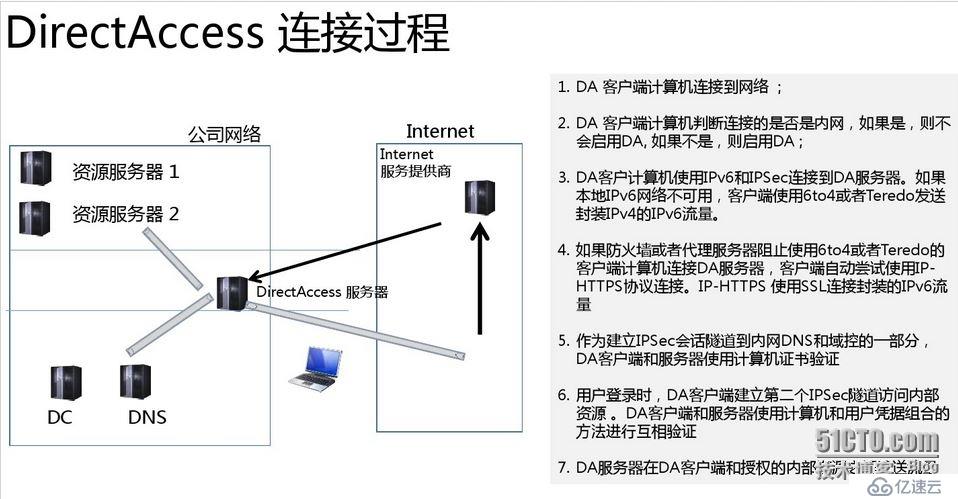
最开始是看的英文书,看得有点晕,所以后来去搜了上面的中文资料。看懂了中文,再看英文解释就会觉得更好理解了。现在把英语的也贴上来做参考
This general process can be broken down into the following specific steps:
1. The DirectAccess client computer running Windows 8, Windows 7 Enterprise, or
Windows 7 Ultimate detects that it is connected to a network.
2. The DirectAccess client computer determines whether it is connected to the intranet. If
the client is connected to the intranet, it does not use DirectAccess.
3. The DirectAccess client connects to the DirectAccess server by using IPv6 and IPsec.
4. If the client is not using IPv6, it will try to use 6to4 or Teredo tunneling to send
IPv4-encapsulated IPv6 traffic.
5. If the client cannot reach the DirectAccess server using 6to4 or Teredo tunneling, the
client tries to connect using the Internet Protocol over Hypertext Transfer Protocol Secure
(IP-HTTPS) protocol. IP-HTTPS uses a Secure Sockets Layer (SSL) connection to
encapsulate IPv6 traffic.
6. As part of establishing the IPsec session for the tunnel to reach the intranet DNS server
and domain controller, the DirectAccess client and server authenticate each other using
computer certificates for authentication.
7. If Network Access Protection (NAP) is enabled and configured for health validation, the
Network Policy Server (NPS) determines whether the client is compliant with system
health requirements. If it is compliant, the client receives a health certificate, which is
submitted to the DirectAccess server for authentication.
8. When the user logs on, the DirectAccess client establishes a second IPsec tunnel to access
the resources of the intranet. The DirectAccess client and server authenticate each other
using a combination of computer and user credentials.
9. The DirectAccess server forwards traffic between the DirectAccess client and the intranet
resources to which the user has been granted access.
The Name Resolution Policy Table (NRPT) is used to determine the behavior of the DNS
clients when issuing queries and processing so that internal resources are not exposed to the
public via the Internet and to separate traffic that isn’t DirectAccess Internet traffic from
DirectAccess Internet traffic. By using the NRPT, the DirectAccess clients use the intranet
DNS servers for internal resources and Internet DNS for name resolution of other resources.
The NRPT is managed using group policies, specifically, Computer Configuration\Policies\
Windows Settings\Name Resolution Policy.
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。