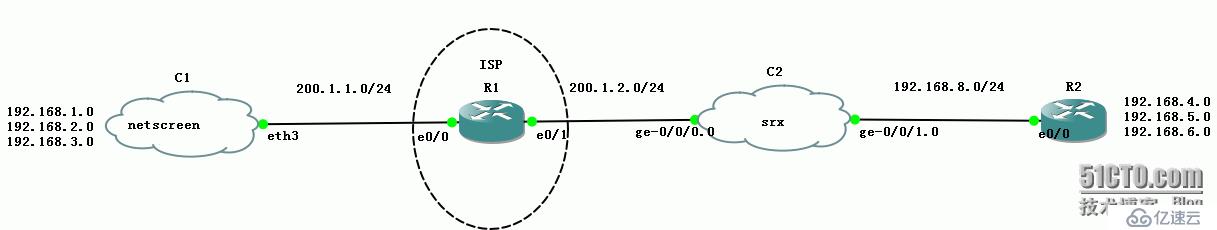
拓扑:
Netscreen Configuration:
set zone name y1
set interface "tunnel.1" zone "y1"
set interface "loopback.1" zone "Home"
set interface "loopback.2" zone "Home"
set interface "loopback.3" zone "Home"
set interface ethernet3 ip 200.1.1.2/24
set interface loopback.1 ip 192.168.1.1/24
set interface loopback.2 ip 192.168.2.1/24
set interface loopback.3 ip 192.168.3.1/24
set interface tunnel.1 ip 172.16.1.1/24
set interface ethernet3 manage
set interface loopback.1 manage
set interface loopback.2 manage
set interface loopback.3 manage
set address "Home" "192.168.1.0" 192.168.1.0 255.255.255.0
set address "Home" "192.168.2.0" 192.168.2.0 255.255.255.0
set address "Home" "192.168.3.0" 192.168.3.0 255.255.255.0
set address "y1" "192.168.4.0" 192.168.4.0 255.255.255.0
set address "y1" "192.168.5.0" 192.168.5.0 255.255.255.0
set address "y1" "192.168.6.0" 192.168.6.0 255.255.255.0
set address "y1" "192.168.8.0" 192.168.8.0 255.255.255.0
set group address "Home" "zongbu"
set group address "Home" "zongbu" add "192.168.1.0"
set group address "Home" "zongbu" add "192.168.2.0"
set group address "Home" "zongbu" add "192.168.3.0"
set group address "y1" "y1-add"
set group address "y1" "y1-add" add "192.168.4.0"
set group address "y1" "y1-add" add "192.168.5.0"
set group address "y1" "y1-add" add "192.168.6.0"
set group address "y1" "y1-add" add "192.168.8.0"
set ike gateway "to-y1" address 200.1.2.2 Main outgoing-interface "ethernet3" preshare "Gxl2rRLGNckqmts4QACGowXnN2nJ8eFsew==" sec-level standard
set *** "y1" gateway "to-y1" no-replay tunnel idletime 0 sec-level standard
set *** "y1" id 0x1 bind interface tunnel.1
set *** "y1" proxy-id local-ip 0.0.0.0/0 remote-ip 0.0.0.0/0 "ANY"
set policy id 6 from "y1" to "Home" "y1-add" "zongbu" "ANY" permit
set policy id 5 from "Home" to "y1" "zongbu" "y1-add" "ANY" permit
set vrouter trust-vr protocol ospf
set vrouter trust-vr protocol ospf enable
set vrouter trust-vr protocol ar 0
set router-id 1.1.1.1
set route 0.0.0.0/0 interface ethernet3 gateway 200.1.1.1
set interface loopback.1 protocol ospf area 0.0.0.0
set interface loopback.1 protocol ospf enable
set interface loopback.2 protocol ospf area 0.0.0.0
set interface loopback.2 protocol ospf enable
set interface loopback.3 protocol ospf area 0.0.0.0
set interface loopback.3 protocol ospf enable
set interface tunnel.1 protocol ospf area 0.0.0.0
set interface tunnel.1 protocol ospf ignore-mtu 本实验最重要的命令,不敲则ospf邻居卡在exstart状态
set interface tunnel.1 protocol ospf enable
ISP Configurationg:
int e0/0
ip add 200.1.1.1 255.255.255.0
no sh
int e0/1
ip add 200.1.2.1 255.255.255.0
no sh
Juniper SRX Configuration:
version 12.1X44.4;
system {
root-authentication {
encrypted-password "$1$Iq3z9EVf$2Qjh4Bi1SYKIqfaawy9QW/"; ## SECRET-DATA
}
login {
user juniper {
uid 2001;
class super-user;
}
}
services {
ssh;
web-management {
http {
interface ge-0/0/0.0;
}
}
}
syslog {
user * {
any emergency;
}
file messages {
any any;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
license {
autoupdate {
url https://ae1.juniper.net/junos/key_retrieval;
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 200.1.2.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.8.1/24;
}
}
}
st0 {
unit 0 {
family inet {
address 172.16.1.2/24;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 200.1.2.1;
}
}
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/1.0;
interface st0.0;
}
}
}
security {
ike {
policy l2l-p1-gateway {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$s24oGPfz6CuaZz6"; ## SECRET-DATA
}
gateway l2l-p1-gateway {
ike-policy l2l-p1-gateway;
address 200.1.1.2;
external-interface ge-0/0/0.0;
}
}
ipsec {
policy l2l-p2-policy {
proposal-set standard;
}
*** route-*** {
bind-interface st0.0;
ike {
gateway l2l-p1-gateway;
proxy-identity {
local 0.0.0.0/0;
remote 0.0.0.0/0;
service any;
}
ipsec-policy l2l-p2-policy;
}
}
}
screen {
ids-option untrust-screen {
icmp {
ping-death;
}
ip {
source-route-option;
tear-drop;
}
tcp {
syn-flood {
alarm-threshold 1024;
attack-threshold 200;
source-threshold 1024;
destination-threshold 2048;
queue-size 2000; ## Warning: 'queue-size' is deprecated
timeout 20;
}
land;
}
}
}
policies {
from-zone trust to-zone svti {
policy permit-trust-svti {
match {
source-address y1;
destination-address zongbu;
application any;
}
then {
permit;
}
}
}
from-zone svti to-zone trust {
policy permit-svti-trust {
match {
source-address zongbu;
destination-address y1;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0 {
host-inbound-traffic {
system-services {
ping;
telnet;
ssh;
ike;
}
}
}
}
}
security-zone trust {
address-book {
address 192.168.8.0 192.168.8.0/24;
address 192.168.4.0 192.168.4.0/24;
address 192.168.5.0 192.168.5.0/24;
address 192.168.6.0 192.168.6.0/24;
address-set y1 {
address 192.168.8.0;
address 192.168.4.0;
address 192.168.5.0;
address 192.168.6.0;
}
}
interfaces {
ge-0/0/1.0 {
host-inbound-traffic {
system-services {
ping;
}
protocols {
ospf;
}
}
}
}
}
security-zone svti {
address-book {
address 192.168.1.0 192.168.1.0/24;
address 192.168.2.0 192.168.2.0/24;
address 192.168.3.0 192.168.3.0/24;
address-set zongbu {
address 192.168.1.0;
address 192.168.2.0;
address 192.168.3.0;
}
}
host-inbound-traffic {
system-services {
ping;
}
protocols {
ospf;
}
}
interfaces {
st0.0;
}
}
security-zone UN;
}
}
[edit]
R2 configuration:
int e0/0
ip add 192.168.8.2 255.255.255.0
no sh
ip os 110 ar 0
int l0
ip add 192.168.4.1 255.255.255.0
ip os 110 ar 0
int l1
ip add 192.168.5.1 255.255.255.0
ip os 110 ar 0
int l2
ip add 192.168.6.1 255.255.255.0
ip os 110 ar 0
效果图:
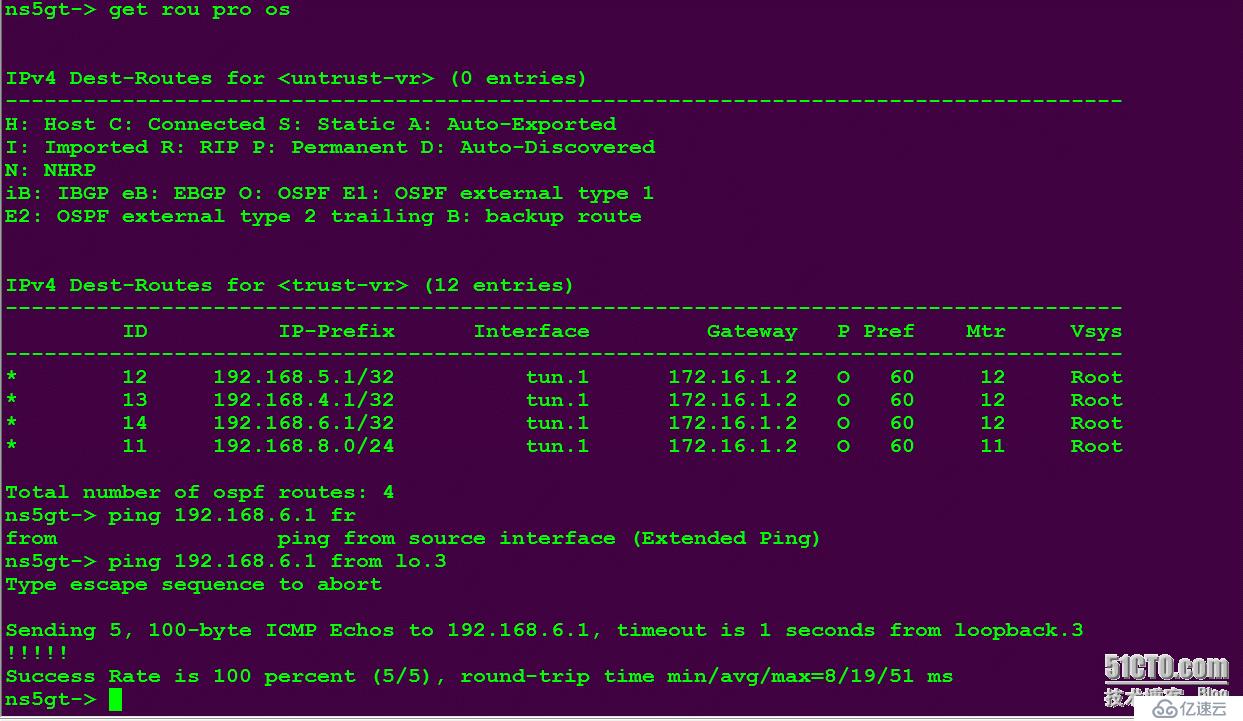
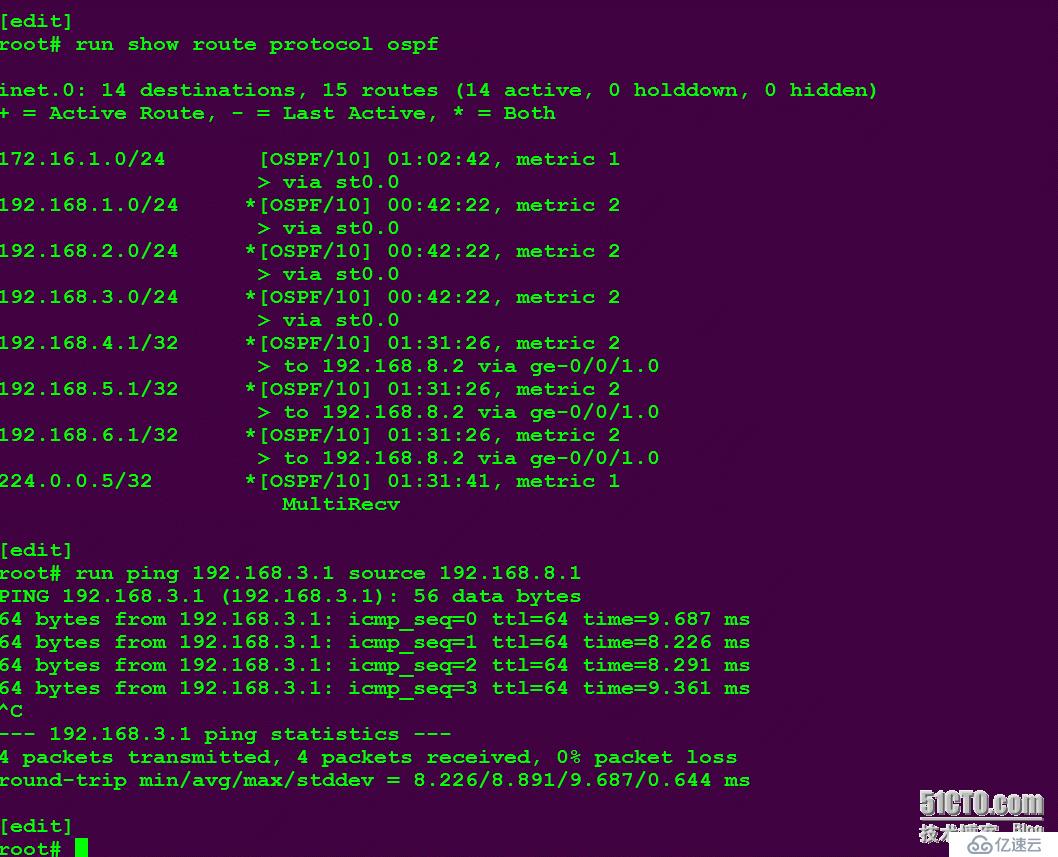
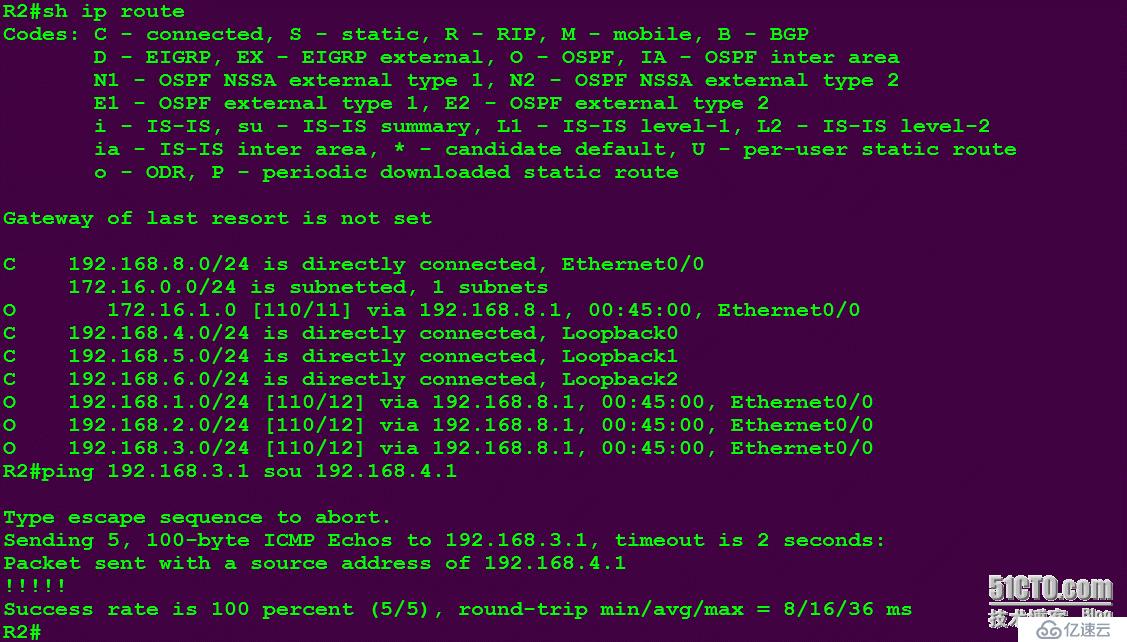
注意一点就OK
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。