本篇内容主要讲解“spring oauth2 +springboot sso的案例分析”,感兴趣的朋友不妨来看看。本文介绍的方法操作简单快捷,实用性强。下面就让小编来带大家学习“spring oauth2 +springboot sso的案例分析”吧!
<dependency>
<groupId>org.springframework.security.oauth.boot</groupId>
<artifactId>spring-security-oauth3-autoconfigure</artifactId>
<version>2.1.6.RELEASE</version>
</dependency>1.服务端需要的是授权与身份验证,通过配置@EnableAuthorizationServer、@EnableWebSecurity、@EnableResourceServer来完成配置。
2.先来配置WebSecurity的配置
package com.example.oauth;
import org.springframework.boot.autoconfigure.security.SecurityProperties;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.annotation.Order;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.BeanIds;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.builders.WebSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.provisioning.InMemoryUserDetailsManager;
/**
* @author sorata
* @date 2019-07-23 09:19
*/
@Configuration
@EnableWebSecurity
@Order(SecurityProperties.BASIC_AUTH_ORDER)
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Bean
public UserDetailsService myUserDetailsService(){
return new InMemoryUserDetailsManager(User.builder().username("admin").password(passwordEncoder().encode("admin")).roles("ADMIN").build());
}
@Bean
public BCryptPasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(myUserDetailsService()).passwordEncoder(passwordEncoder());
}
@Bean(BeanIds.AUTHENTICATION_MANAGER)
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
@Override
public void configure(WebSecurity web) throws Exception {
super.configure(web);
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf().disable().antMatcher("/**")
.authorizeRequests()
.antMatchers("/","/login","/oauth/**").permitAll()
.anyRequest().authenticated()
.and().httpBasic().and().formLogin()
.and().logout();
}
}note:首先是配置用户UserDetailsService,然后配置密码策略。主要的部分是 configure(HttpSecurity http) 方法,这里当我在formLogin()后配置了验证完成转发,即successForwardUrl(“/main”)后,sso客户端请求验证完成时,不会跳转到客户端的请求地址,而是跳转到验证成功的服务端地址 /main。
3.编写一个用户信息的controller
package com.example.oauth;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController;
import java.security.Principal;
/**
* @author sorata
* @date 2019-07-23 09:17
*/
@RestController
public class UserController {
@RequestMapping("/user")
public Principal principal(Principal principal){
return principal;
}
@RequestMapping("/user2")
public Principal principal2(Principal principal){
return principal;
}
}note: 作用就是测试和之后客户端填写的服务器用户信息的url
4.资源服务器
package com.example.oauth;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.oauth3.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth3.config.annotation.web.configuration.ResourceServerConfigurerAdapter;
/**
* @author sorata
* @date 2019-07-23 09:50
*/
@Configuration
@EnableResourceServer
public class ResourceConfig extends ResourceServerConfigurerAdapter {
@Override
public void configure(HttpSecurity http) throws Exception {
http.csrf().disable().antMatcher("/user")
.authorizeRequests().anyRequest().authenticated();
}
}5.完成后的效果
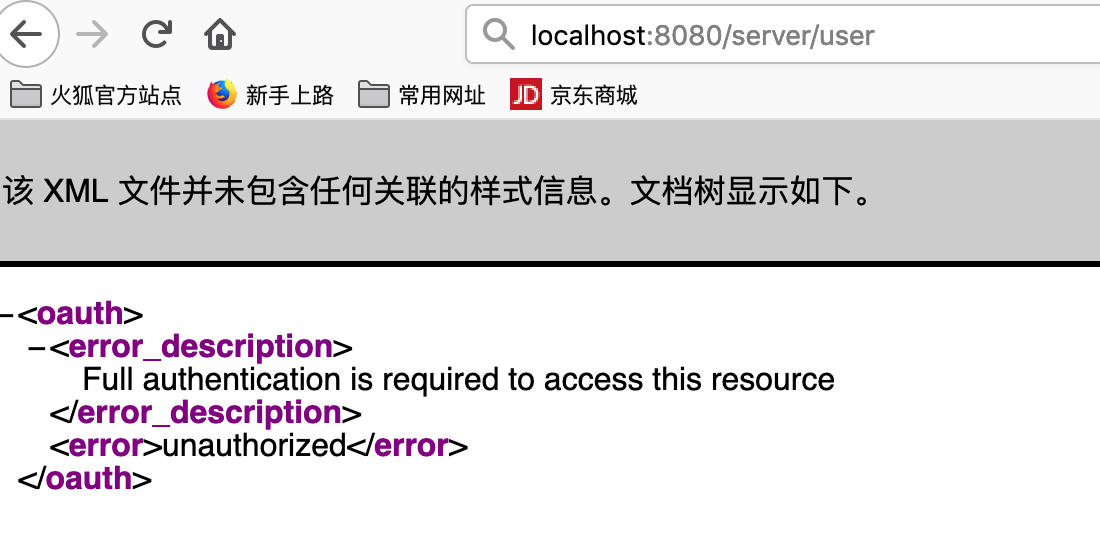
6. 重要的认证服务端
package com.example.oauth;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.oauth3.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth3.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth3.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth3.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth3.config.annotation.web.configurers.AuthorizationServerSecurityConfigurer;
import org.springframework.security.oauth3.provider.token.TokenStore;
import org.springframework.security.oauth3.provider.token.store.InMemoryTokenStore;
/**
* @author sorata
* @date 2019-07-23 10:06
*/
@Configuration
@EnableAuthorizationServer
public class SsoServerConfig extends AuthorizationServerConfigurerAdapter {
@Autowired private AuthenticationManager authenticationManager;
@Autowired private BCryptPasswordEncoder passwordEncoder;
/**
* 如果出现错误 在主类上去掉默认配置
* {@link SsoServerApplication}
*/
@Autowired private UserDetailsService detailsService;
@Override
public void configure(AuthorizationServerSecurityConfigurer security) throws Exception {
security.allowFormAuthenticationForClients()
.tokenKeyAccess("permitAll()")
.checkTokenAccess("isAuthenticated()")
.passwordEncoder(passwordEncoder);
}
@Override
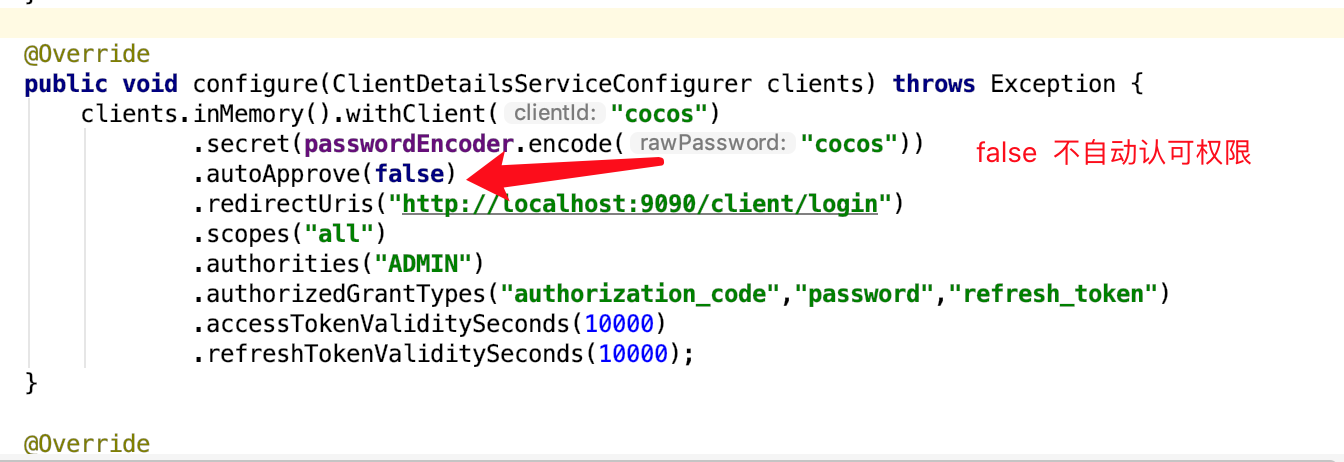
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients.inMemory().withClient("cocos")
.secret(passwordEncoder.encode("cocos"))
.autoApprove(true)
.redirectUris("http://localhost:9090/client/login")
.scopes("all")
.authorities("ADMIN")
.authorizedGrantTypes("authorization_code","password","refresh_token")
.accessTokenValiditySeconds(10000)
.refreshTokenValiditySeconds(10000);
}
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception {
endpoints.authenticationManager(authenticationManager)
.userDetailsService(detailsService).tokenStore(tokenStore());
}
@Bean
public TokenStore tokenStore(){
return new InMemoryTokenStore();
}
}1.客户端实现比较简单,如果想针对行的修改,自定义那么可以根据后面参考地址研读。
2.application.properties
security.oauth3.client.authentication-scheme=form
security.oauth3.client.user-authorization-uri=http://localhost:8080/server/oauth/authorize
security.oauth3.client.access-token-uri=http://localhost:8080/server/oauth/token
security.oauth3.client.client-id=cocos
security.oauth3.client.client-secret=cocos
security.oauth3.resource.user-info-uri=http://localhost:8080/server/user
server.servlet.context-path=/client
server.port=90903.主类添加注解
package com.example.oauth;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.boot.autoconfigure.security.oauth3.client.EnableOAuth3Sso;
@SpringBootApplication
@EnableOAuth3Sso
public class SsoClientApplication {
public static void main(String[] args) {
SpringApplication.run(SsoClientApplication.class, args);
}
}4.用户的接口
package com.example.oauth;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController;
import java.security.Principal;
/**
* @author sorata
* @date 2019-07-23 10:30
*/
@RestController
public class UserController {
@RequestMapping("/user")
public Principal principal(Principal principal){
return principal;
}
} 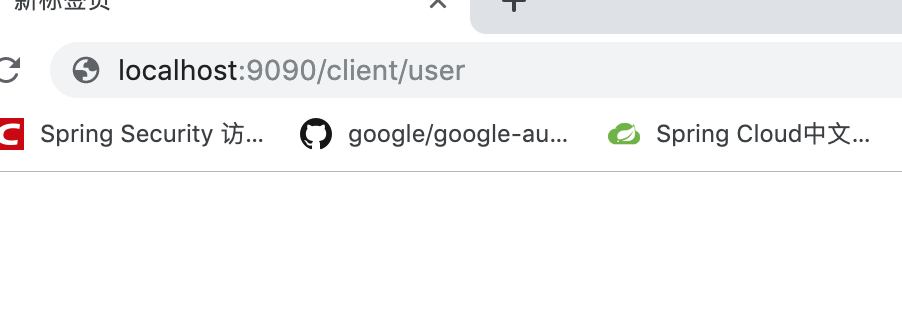
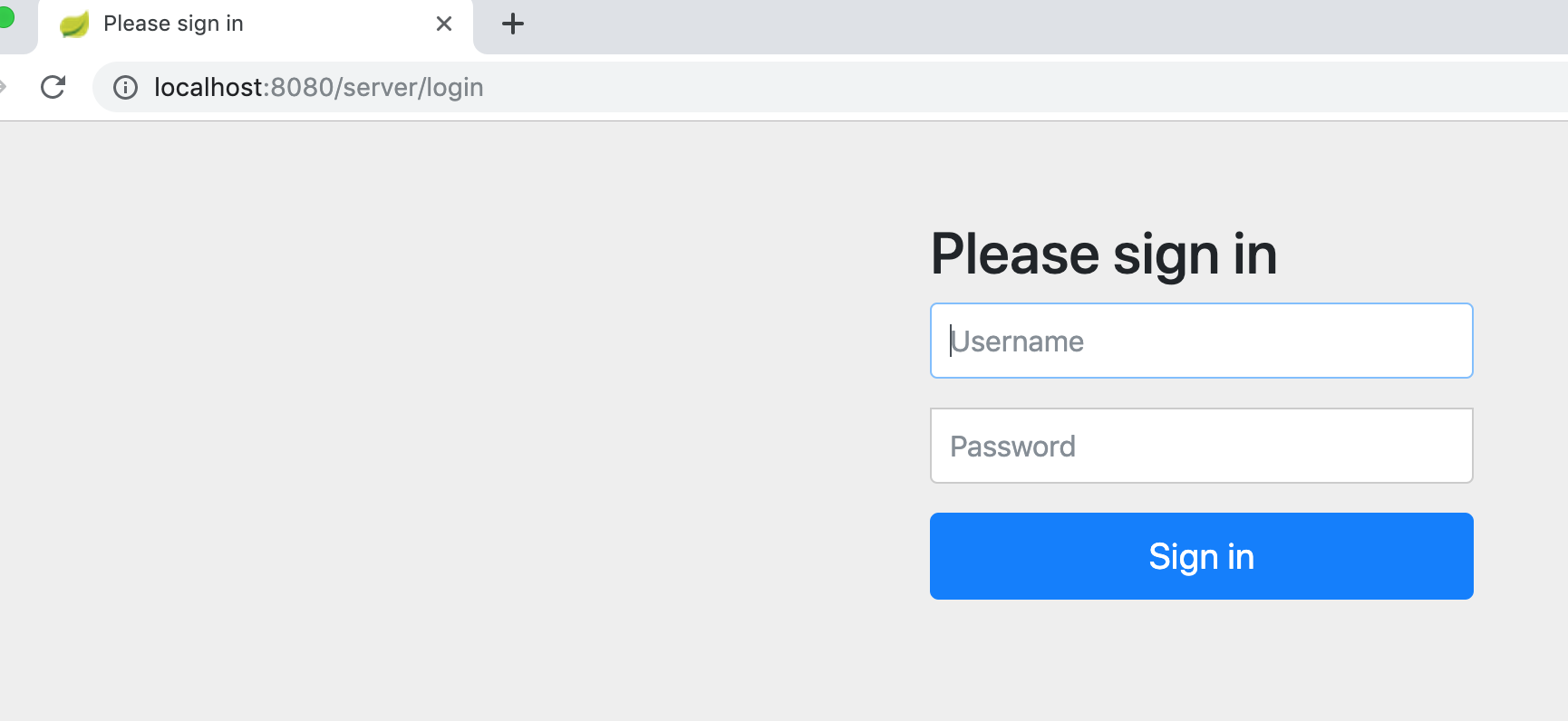
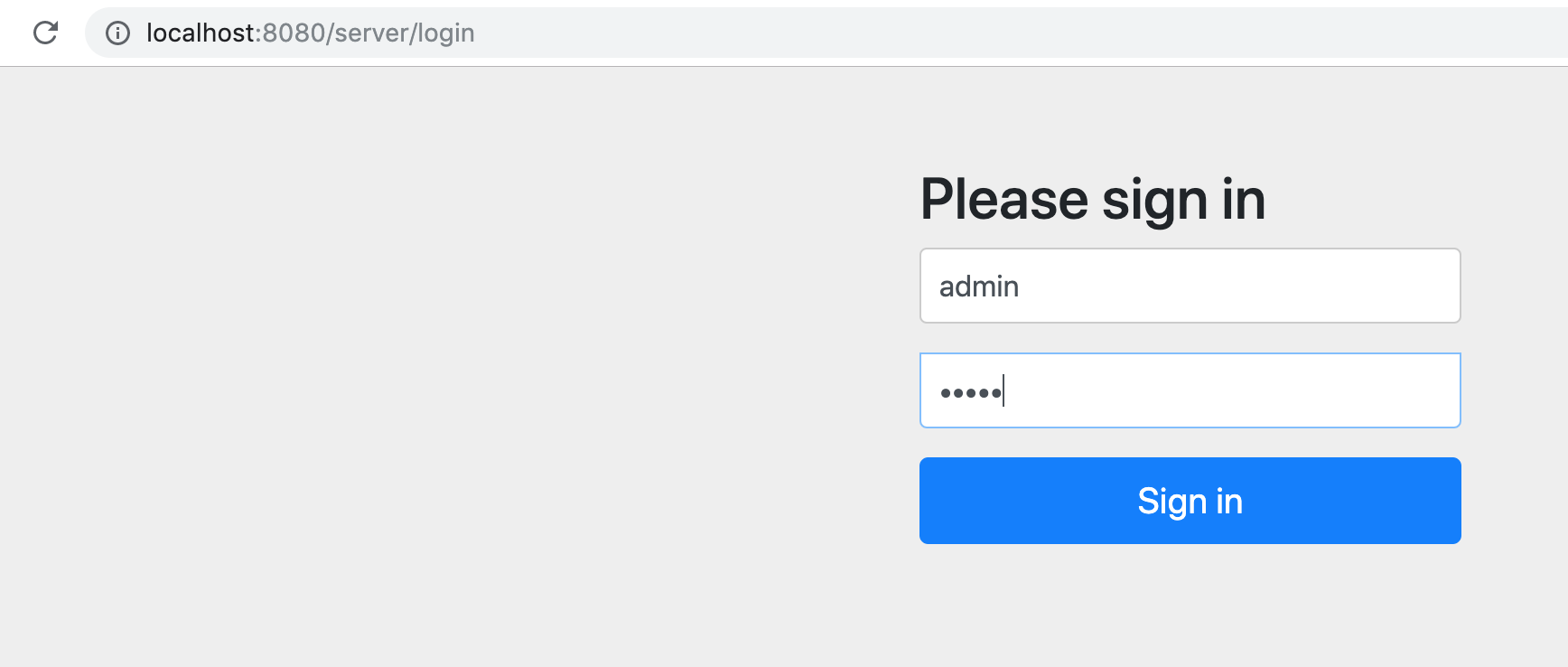
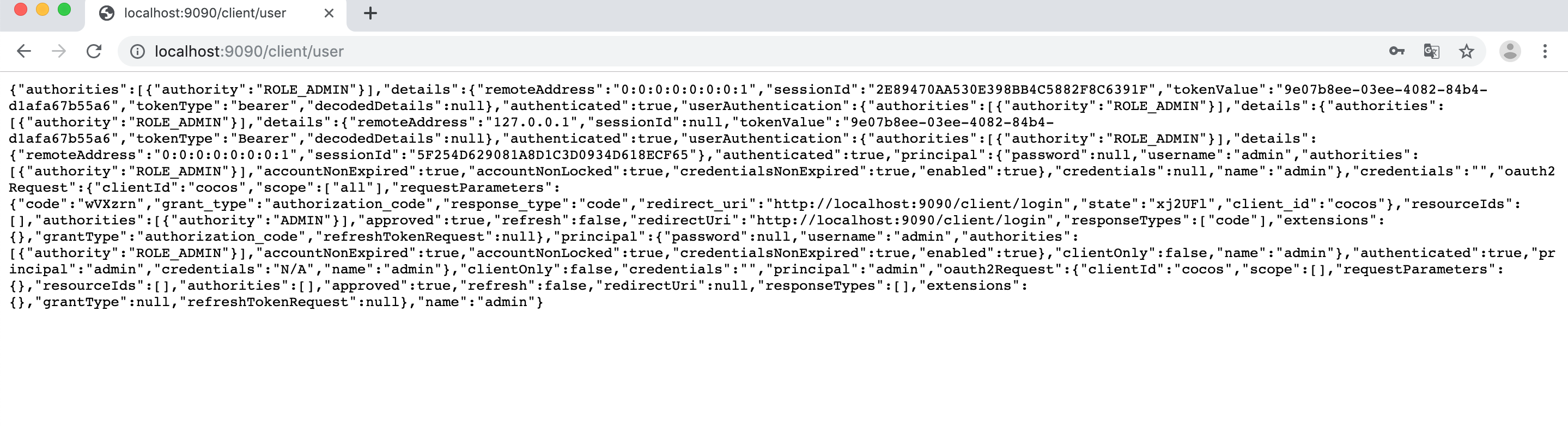
note: 如果想看到
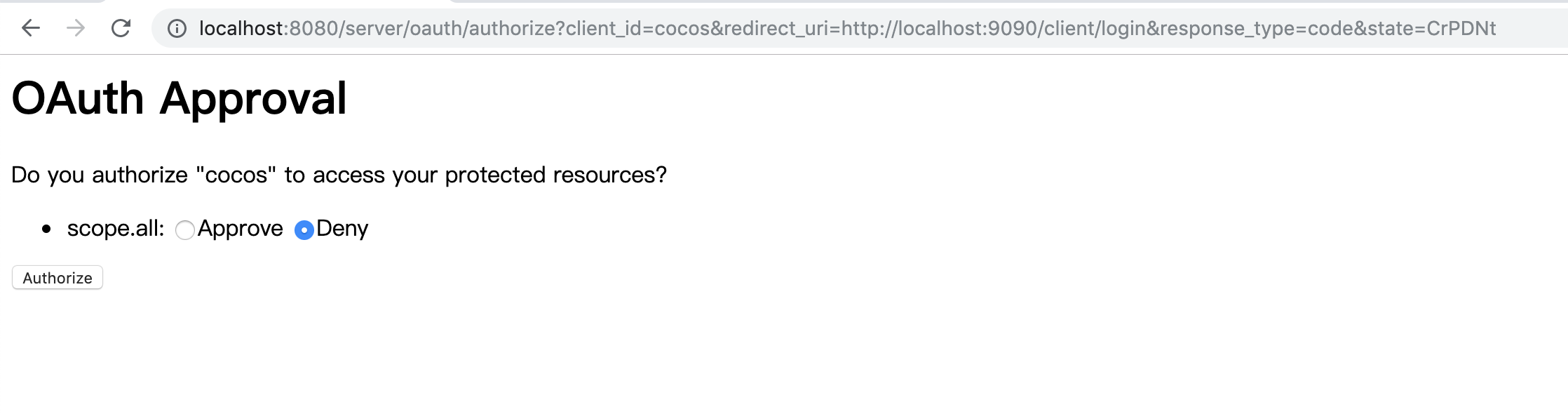
到此,相信大家对“spring oauth2 +springboot sso的案例分析”有了更深的了解,不妨来实际操作一番吧!这里是亿速云网站,更多相关内容可以进入相关频道进行查询,关注我们,继续学习!
亿速云「云服务器」,即开即用、新一代英特尔至强铂金CPU、三副本存储NVMe SSD云盘,价格低至29元/月。点击查看>>
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。
原文链接:https://my.oschina.net/swiftloop/blog/3077724