这篇文章主要介绍了如何使用SpringSecurity实现动态加载权限信息,具有一定借鉴价值,感兴趣的朋友可以参考下,希望大家阅读完这篇文章之后大有收获,下面让小编带着大家一起了解一下。
①数据库中资源与角色对应关系,以及角色和用户对应关系如下图所示:
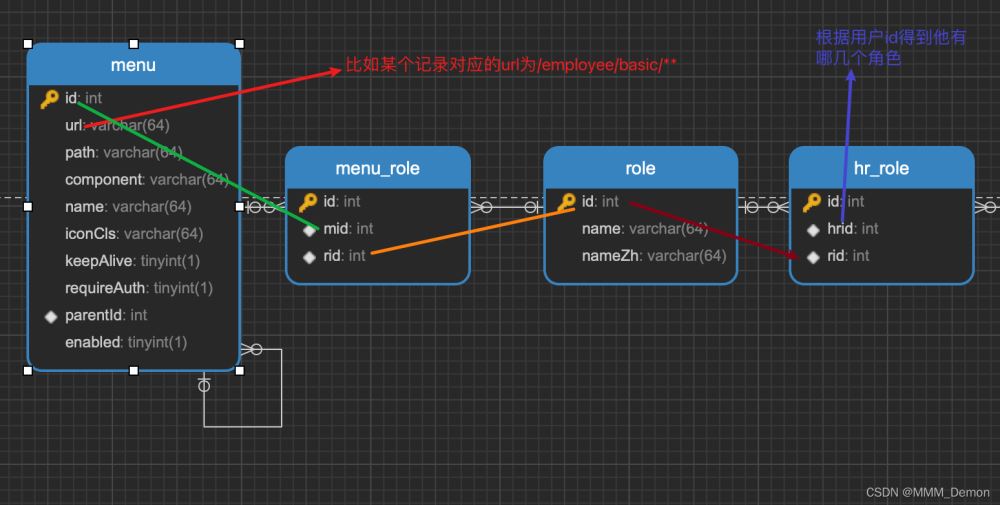
②实现FilterInvocationSecurityMetadataSource类
(1)List<Menu> menus = menuService.getMenusWithRoles();这个是你自己的资源对应角色的查询方法。
(2)重写的support方法都返回true
@Configuration
public class MyFilterInvocation implements FilterInvocationSecurityMetadataSource {
@Autowired
private MenuService menuService;
AntPathMatcher antPathMatcher = new AntPathMatcher();
@Override
public Collection<ConfigAttribute> getAttributes(Object object) throws IllegalArgumentException {
String requestUrl = ((FilterInvocation) object).getRequestUrl();
List<Menu> menus = menuService.getMenusWithRoles();
//- 遍历数据库的url,看请求路径是否与其匹配
for (Menu menu : menus) {
//- 如果请求路径和数据库的路径匹配
if (antPathMatcher.match(menu.getUrl(),requestUrl)){
//- 访问该路径需要的角色
List<Role> roles = menu.getRoles();
String[] strs = new String[roles.size()];
for (int i = 0; i < roles.size(); i++) {
strs[i] = roles.get(i).getName();
}
return SecurityConfig.createList(strs);
}
}
//- 如果请求路径和数据库的所有路径都不匹配,说明这个资源是登录后即可访问的
//- 用户登录即可访问,相当于在SecurityConfig中配置了.anyRequest().authenticated()
return SecurityConfig.createList("ROLE_LOGIN");
}
@Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
return null;
}
@Override
public boolean supports(Class<?> clazz) {
return true;
}
}③实现AccessDecisionManager类
重写的support方法都返回true
@Configuration
public class MyDecisionManager implements AccessDecisionManager {
@Override
public void decide(Authentication authentication, Object object, Collection<ConfigAttribute> configAttributes) throws AccessDeniedException, InsufficientAuthenticationException {
for (ConfigAttribute configAttribute : configAttributes) {
String needRole = configAttribute.getAttribute();
if ("ROLE_LOGIN".equals(needRole)) {
//- 用户登录即可访问,相当于在SecurityConfig中配置了.anyRequest().authenticated()
if (authentication instanceof AnonymousAuthenticationToken) {
throw new AccessDeniedException("尚未登录,请先登录");
} else {
return;
}
}
Collection<? extends GrantedAuthority> authorities = authentication.getAuthorities();
//这里我写的是只要访问该资源的用户具有`访问该资源所需要角色`的其中一个即可
for (GrantedAuthority authority : authorities) {
if (authority.getAuthority().equals(needRole)) {
return;
}
}
}
throw new AccessDeniedException("权限不足,请联系管理员");
}
@Override
public boolean supports(ConfigAttribute attribute) {
return true;
}
@Override
public boolean supports(Class<?> clazz) {
return true;
}
}④到SecurityConfig配置类中完成相应配置
@Autowired
private MyDecisionManager myDecisionManager;
@Autowired
private MyFilterInvocation myFilterInvocation;
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.withObjectPostProcessor(new ObjectPostProcessor<FilterSecurityInterceptor>() {
@Override
public <O extends FilterSecurityInterceptor> O postProcess(O object) {
object.setAccessDecisionManager(myDecisionManager);
object.setSecurityMetadataSource(myFilterInvocation);
return object;
}
});
http.exceptionHandling().accessDeniedHandler(myAccessDeniedHandler());
}
@Bean
MyAccessDeniedHandler myAccessDeniedHandler(){
return new MyAccessDeniedHandler();
}⑤可选,实现AccessDeniedHandler类
public class MyAccessDenied implements AccessDeniedHandler {
@Override
public void handle(HttpServletRequest req, HttpServletResponse resp, AccessDeniedException accessDeniedException) throws IOException, ServletException {
resp.setContentType("application/json;charset=utf-8");
PrintWriter pw = resp.getWriter();
pw.write(new ObjectMapper().writeValueAsString(RespBean.error("权限不够,请联系管理员")));
pw.flush();
pw.close();
}
}感谢你能够认真阅读完这篇文章,希望小编分享的“如何使用SpringSecurity实现动态加载权限信息”这篇文章对大家有帮助,同时也希望大家多多支持亿速云,关注亿速云行业资讯频道,更多相关知识等着你来学习!
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。