本文是小弟整合几位大神的文章,见笑@@
Linux利用sendmail和fetion发送报警通知
nagios监控windows主机 && linux主机
CentOS 5/6.X 使用 EPEL YUM源:
实验环境:
两台64位的centos-6.6
一台window-server-2003
安装网络yum源:
centos5.x--32位
[root@centos-server ~]# wget http://mirrors.yun-idc.com/epel/5/i386/epel-release-5-4.noarch.rpm
centos5.x--64位
[root@centos-server ~]# wget http://mirrors.hust.edu.cn/epel//5/x86_64/epel-release-5-4.noarch.rpm
centos6.x--32位
[root@centos-server ~]# wget http://download.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
centos6.x--64位
[root@centos-server ~]# wget http://mirrors.hust.edu.cn/epel//6/x86_64/epel-release-6-8.noarch.rpm
[root@centos-server ~]# rpm -ivh epel-release-6-8.noarch.rpm搭建nagios监控服务器:
yum install httpd php* openssl openssl-devel nagios nagios-plugins*
setenforce 0
iptables -I INPUT -p tcp --dport 80 -j ACCEPT
增加httpd的访问验证
[root@centos-server ~]# htpasswd -c /etc/nagios/htpasswd nagiosadmin
New password:
Re-type new password:
Adding password for user nagiosadmin
注意nagios的默认用户就是nagiosadmin,如果你使用的不是此用户,需要修改以下项目
[root@centos-server objects]# cat /etc/nagios/cgi.cfg |grep nagiosadmin
authorized_for_system_information=nagiosadmin
authorized_for_configuration_information=nagiosadmin
authorized_for_system_commands=nagiosadmin
authorized_for_all_services=nagiosadmin
authorized_for_all_hosts=nagiosadmin
authorized_for_all_service_commands=nagiosadmin
authorized_for_all_host_commands=nagiosadmin
快速修改命令
[root@centos-server ~]# sed -i 's/nagiosadmin/dragon/g' /etc/nagios/cgi.cfg
通过httpd访问nagios的web文件
[root@centos-server objects]# cat >> /etc/httpd/conf/httpd.conf <<END
scriptAlias /nagios/cgi-bin "/usr/lib64/nagios/cgi-bin/"
<Directory "/usr/lib64/nagios/cgi-bin/">
AllowOverride AuthConfig
Options ExecCGI
Order allow,deny
Allow from all
AuthUserFile /etc/nagios/htpasswd
</Directory>
Alias /nagios /usr/share/nagios/html/
<Directory "/usr/share/nagios/html/">
Options None
AllowOverride AuthConfig
Order allow,deny
Allow from all
AuthUserFile /etc/nagios/htpasswd
</Directory>
END定义监控LINUX文件:
[root@centos-server objects]# mkdir /etc/nagios/objects/server
[root@centos-server objects]# vim /etc/nagios/nagios.cfg
cfg_dir=/usr/local/nagios/etc/servers
[root@centos-server objects]# vim /etc/nagios/objects/server/192.168.150.143.cfg
define host{
use linux-server
host_name 192.168.150.143
alias linux
address 192.168.150.143
}
define service{
use generic-service
host_name 192.168.150.143
service_description Check Swap
check_command check_nrpe!check_swap
}
define service{
use generic-service
host_name 192.168.150.143
service_description total
check_command check_nrpe!check_total_procs
}
define service{
use generic-service
host_name 192.168.150.143
service_description check_load
check_command check_nrpe!check_load
}
define service{
use generic-service
host_name 192.168.150.143
service_description check_tcp_3306
check_command check_tcp!3306
}
define service{
use generic-service
host_name 192.168.150.143
service_description check_users
check_command check_nrpe!check_users
}
define service{
use generic-service
host_name 192.168.150.143
service_description check_mysql
check_command check_nrpe!check_mysql
}
define service{
use generic-service
host_name 192.168.150.143
service_description check_http 192.168.150.143/index.html
check_command check_http!'-u /index.html'
}
define service{
use generic-service
host_name 192.168.150.143
service_description check_disk
check_command check_nrpe!check_sda1
}
在commonds.cfg中添加check_nrpe的命令
[root@centos-server objects]# vim /etc/nagios/objects/commands.cfg
define command{
command_name check_nrpe
command_line $USER1$/check_nrpe -H $HOSTADDRESS$ -c $ARG1$
}配置linux客户端:
[root@centos-server ~]# yum install nagios-plugins* openssl-devel openssl mysql-server
[root@centos-server ~]# cat /etc/nrpe.d/nrpe
only_from=127.0.0.1 192.168.150.139
[root@centos-server objects]# vim /etc/nagios/nrpe.cfg
添加nagios监控端的ip
allowed_hosts=127.0.0.1,192.168.150.139
添加以下内容
command[check_users]=/usr/lib64/nagios/plugins/check_users -w 5 -c 10
command[check_load]=/usr/lib64/nagios/plugins/check_load -w 15,10,5 -c 30,25,20
command[check_sda1]=/usr/lib64/nagios/plugins/check_disk -w 20% -c 10% -p /dev/sda1
command[check_zombie_procs]=/usr/lib64/nagios/plugins/check_procs -w 5 -c 10 -s Z
command[check_total_procs]=/usr/lib64/nagios/plugins/check_procs -w 150 -c 200
command[check_mysql]=/usr/lib64/nagios/plugins/check_mysql -H 127.0.0.1 -ubbq -pqwe123 #此用户需要在mysql中添加
command[check_swap]=/usr/lib64/nagios/plugins/check_swap -w 20% -c 10%通过yum安装的nagios监控插件还有很多,有需要用到的可以研究下:
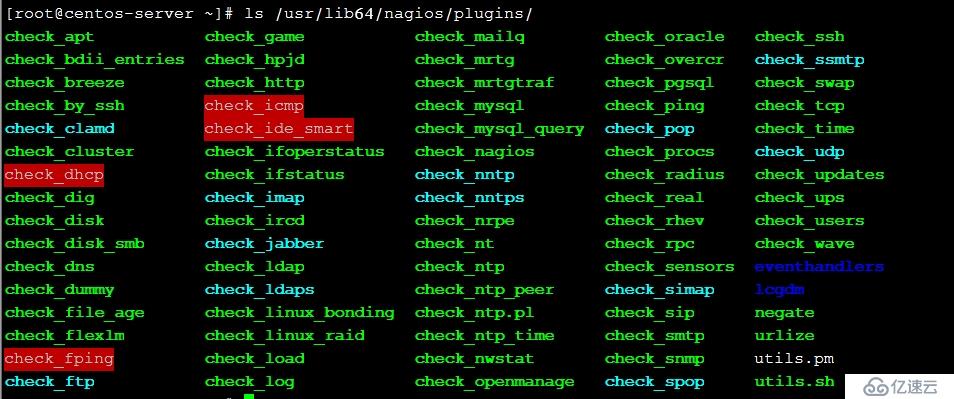
两端重启服务:
service nagios restart
service httpd restart
service nrpe restart
service xinetd restart
[root@centos-server ~]# netstat -anl|grep 5666
tcp 0 0 0.0.0.0:5666 0.0.0.0:* LISTEN
tcp 0 0 :::5666 :::* LISTEN
在nagios监控端测试被监控端nrpe联通:
[root@centos-server ~]# /usr/lib64/nagios/plugins/check_nrpe -H 192.168.150.143
NRPE v2.15监控window-server:
[root@centos-server objects]# vim /etc/nagios/objects/server/192.168.150.146.cfg
define host{
usewindows-server
host_name 192.168.150.146
alias my computer
address 192.168.150.146
}
define service{
use generic-service
host_name 192.168.150.146
service_description NSClient++ Version
check_command check_win!CLIENTVERSION
}
define service{
use generic-service
host_name 192.168.150.146
service_description Uptime
check_command check_win!UPTIME
}
define service{
use generic-service
host_name 192.168.150.146
service_description CPU Load
check_command check_win!CPULOAD!-l 5,80,90
}
define service{
use generic-service
host_name 192.168.150.146
service_description Memory Usage
check_command check_win!MEMUSE!-w 80 -c 90
}
define service{
use generic-service
host_name 192.168.150.146
service_description C:\ Drive Space
check_command check_win!USEDDISKSPACE!-l c -w 80 -c 90
}
define service{
use generic-service
host_name 192.168.150.146
service_description D:\ Drive Space
check_command check_win!USEDDISKSPACE!-l d -w 80 -c 90
}
define service{
use generic-service
host_name 192.168.150.146
service_description E:\ Drive Space
check_command check_win!USEDDISKSPACE!-l e -w 80 -c 90
}
define service{
use generic-service
host_name 192.168.150.146
service_description Explorer
check_command check_win!PROCSTATE!-d SHOWALL -l Explorer.exe
}
[root@centos-server objects]# vim /etc/nagios/objects/commands.cfg
define command{
command_name check_win
command_line $USER1$/check_nt -H "$HOSTADDRESS$" -p 12489 -s dianyi123 -v $ARG1$ $ARG2$
}测试配置文件:
[root@centos-server objects]# /usr/sbin/nagios -v /etc/nagios/nagios.cfg
Error: Could not find any hostgroup matching 'windows-servers' (config file '/etc/nagios/objects/server/192.168.150.146.cfg', starting on line 1)
#这里我遇到这个错误了,把/etc/nagios/objects/templates.cfg 里window-server模版主机中以下这项注释就可以了
#hostgroups windows-servers ;
重启以下服务
[root@centos-server objects]# service nagios restart配置window安装NSClient++:
1.
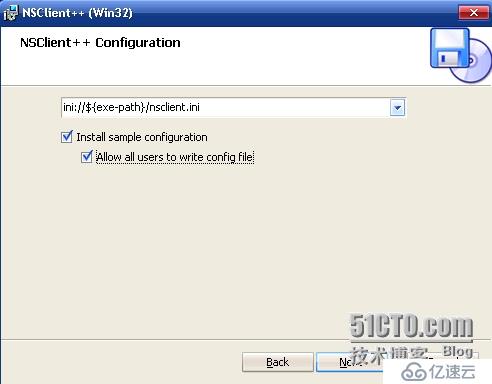
2.
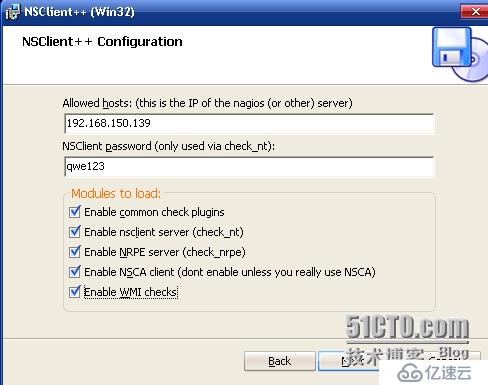
3.
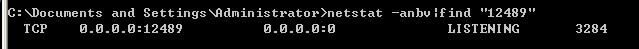
看到监控结果:
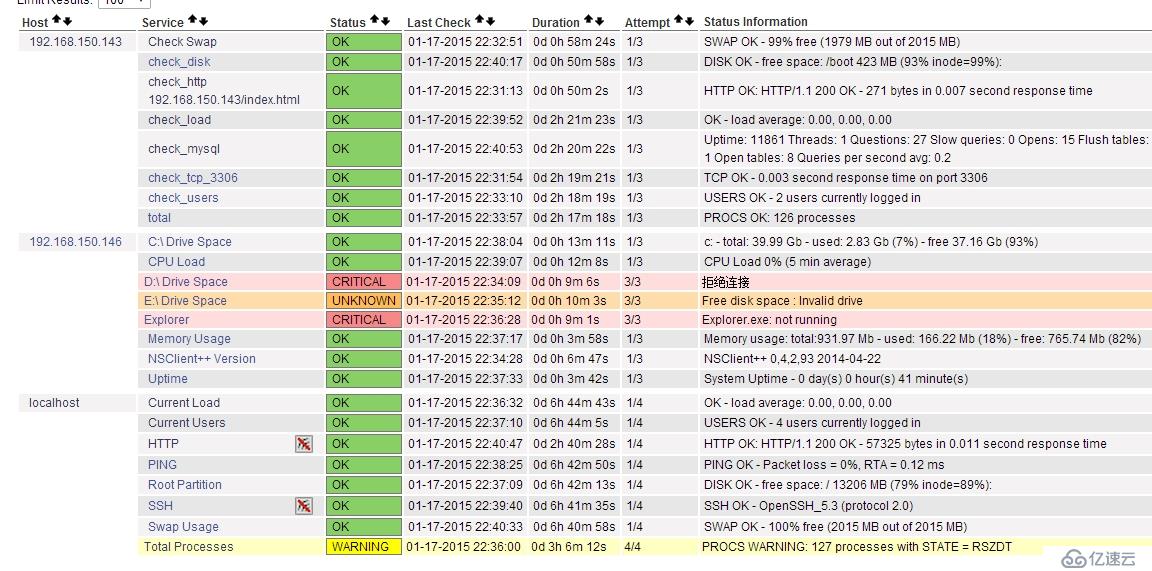
邮件报警设置:
引用郑彦生的原文
1、停止系统自带的sendmail服务
# /etc/init.d/postfix stop
2、安装sendmail和mailx
# yum -y install sendmail mailx
3、修改sendmail配置文件
# cp /etc/mail.rc /etc/mail.rc.bak
# cat >> /etc/mail.rc << EOF
set from=13260071987@139.com smtp=smtp.139.com
set smtp-auth-user=13260071987@139.com smtp-auth-password=yi15093547036 smtp-auth=login
EOF
4、重新启动sendmail服务
# service sendmail restart
5.修改联系人
[root@centos-server objects]# vim /etc/nagios/objects/contacts.cfg
define contact{
contact_name nagiosadmin
use generic-contact
alias Nagios Admin
email 18507656225@139.com
}查看邮件:
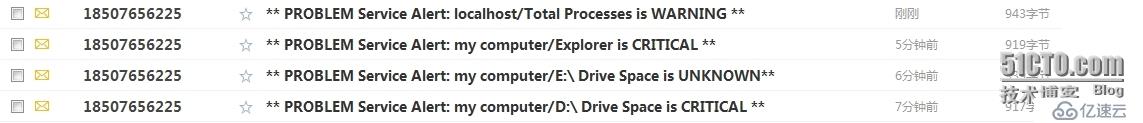
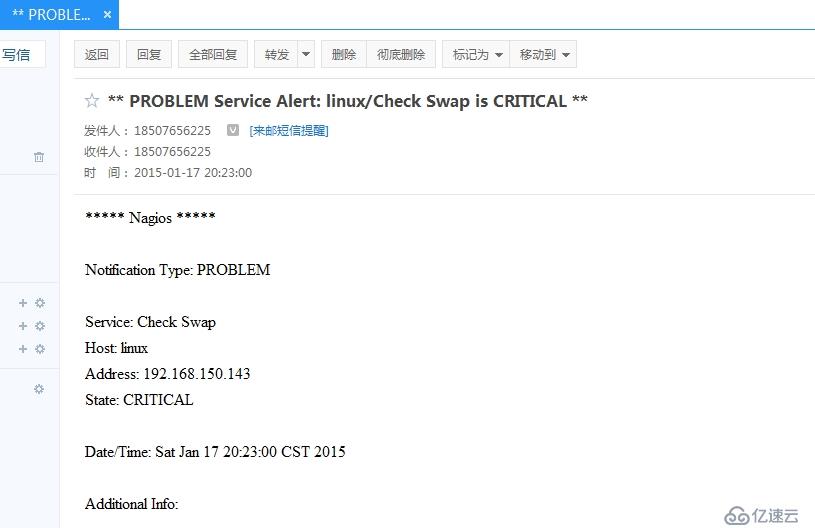
亿速云「云服务器」,即开即用、新一代英特尔至强铂金CPU、三副本存储NVMe SSD云盘,价格低至29元/月。点击查看>>
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。