基于用户的MPF
username user1 password cisco
username user2 password cisco
!
!创建两个账号给用户认证用
object-group user group1
!
!创建一个对象组
user Local\user1
!
!匹配本地数据的用户,也可以是ACS。
object-group user group2
user Local\user2
access-list 100 extended permit tcp any any eq 80
!
!匹配流量
aaa authentication match 100 inside LOCAL
!
!只要是这些流量都做认证,认证数据库为本地
access-list
filter-shrun
permit tcp
object-group-user
group1 any
any eq www
!
!匹配流量,并且是用户1的。
access-list
filter-who
permit tcp
object-group-user group2 any
any
eq www
regex who "who"
!
!配置正则表达式,有”who”关键字的
regex shrun "sh/run"
class-map class1
match access-list
filter-shrun
!!
匹配流量
class-map class2
match access-list filter-who
policy-map type inspect http policy-map1
!!
注意,这是5-7层
parameters
match request uri regex shrun
!
!当这个流量中,有正则表达式里的关键字时
drop-connection log
!
!丢弃并且做log
policy-map type inspect http policy-map2
parameters
match request uri regex who
reset
policy-map global_policy
class class1
inspect http policy-map1
!!
深度过滤
class class2
inspect http policy-map2Botnet Traffic Filter
ASDM自行添加即可
NAT
Object NAT:只能转换源或目的IP
Twice NAT:在满足策略下转换源和目IP
静态(常用于指定服务器对外端口转换),PAT(动态地址加端口转换),identity NAT(旁路部分地址)
一个网段转换一个地址范围
配置动态NAT
object network innet
subnet 192.168.17.0 255.255.255.0
object network outnet
range 192.168.16.60 192.168.16.70
object network innet
nat (inside,outside) dynamic outnet
查看
ASA(config)# show xlate
1 in use, 1 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.17.100 to outside:192.168.16.65 flags i idle 0:01:03 timeout 3:00:00
ASA(config)# show running-config nat
!
object network innet
nat (inside,outside) dynamic outnet
ASA(config)# show running-config object network
object network innet
subnet 192.168.17.0 255.255.255.0
object network outnet
range 192.168.16.60 192.168.16.70
ASA(config)# show running-config timeout
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
..
更改nat超时时间
ASA(config)# timeout xlate 1:0:0
清除转换表
ASA(config)# clear xlate静态nat
把动态的 object中的网段范围换成host 再改静态就可以了一个范围转换一个地址不同端口
PAT
!
object network innet
nat (inside,DMZ) dynamic 192.168.12.110 //直接指向一个地址即可
ASA# show xlate
1 in use, 2 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
TCP PAT from inside:192.168.17.100/49526 to DMZ:192.168.12.110/49526 flags ri idle 0:01:15 timeout 0:00:30先动态转换,地址池用尽再切换PAT
object network outpool
range 192.168.16.119 192.168.16.120
object network innet
subnet 7.7.7.0 255.255.255.0
!
object network innet
nat (inside,outside) dynamic outpool interface //若地址池用尽就用接口的ip做pat

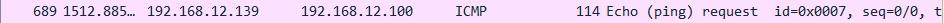

ASA# show x
4 in use, 4 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
ICMP PAT from inside:7.7.7.1/14 to DMZ:192.168.12.139/14 flags ri idle 0:00:04 timeout 0:00:30
NAT from inside:7.7.7.3 to DMZ:192.168.12.119 flags i idle 0:00:08 timeout 1:00:00
NAT from inside:7.7.7.2 to DMZ:192.168.12.120 flags i idle 0:00:06 timeout 1:00:00
ICMP PAT from inside:7.7.7.7/15 to DMZ:192.168.12.139/15 flags ri idle 0:00:01 timeout 0:00:30PAT地址池
nat (inside,DMZ) dynamic pat-pool dmzpool round-robin
动态转换到dmzpool里的地址的不同端口 round-robin表示轮询地址池里的地址ASA(config-network-object)# show x
4 in use, 4 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
ICMP PAT from inside:7.7.7.1/22 to DMZ:192.168.12.119/22 flags ri idle 0:00:03 timeout 0:00:30
ICMP PAT from inside:7.7.7.3/20 to DMZ:192.168.12.119/20 flags ri idle 0:00:07 timeout 0:00:30
ICMP PAT from inside:7.7.7.2/21 to DMZ:192.168.12.120/21 flags ri idle 0:00:05 timeout 0:00:30
ICMP PAT from inside:7.7.7.7/23 to DMZ:192.168.12.120/23 flags ri idle 0:00:01 timeout 0:00:30静态PAT
object network DMZ_Web_Server
host 192.168.12.100
nat (DMZ,outside) static interface service tcp www www // ftp 2121 等等
//注: 有这句,能访问192.168.16.139,但不能访问192.168.12.100
没有这句,能访问192.168.12.100
access-list out-dmz extended permit tcp any object DMZ_Web_Server eq www
access-group out-dmz in interface outsideASA(config-network-object)# show x
1 in use, 4 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
TCP PAT from DMZ:192.168.12.100 80-80 to outside:192.168.16.139 80-80
flags sr idle 0:02:40 timeout 0:00:00outside 口抓包:

dmz口抓包:

Static NAT DNS Rewrite
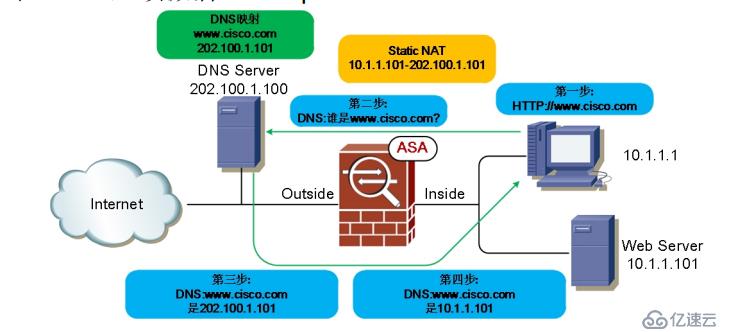
注:在ASA上必须激活DNS inspection
object network Inside-Web-Server
host 10.1.1.101
object network Inside-Web-Server
nat (Inside,Outside) static 202.100.1.101 dns篡改dns解析的地址,内网访问www.cisco.com实际上是访问内网的一台web服务器
Dynamic Identity NAT
Dynamic Identity NAT转换本地地址到相同的地址,到低安全级别的接口。(只能高到低)
Outbound流量会在转换表中产生一个临时的转换槽位。
Static Identity NAT
同上,不过是永久表项
Twice Nat
只有源目符合的才会被匹配转换,
若只从object nat 中旁路一些数据包(由此可见,twice nat 默认优先 object nat),可以把转换前后设置一致,类似identity nat,当然也可以设置其他(如***配置)
object network dst-1
host 1.1.1.1
object network dst-202
host 202.100.1.1
object network pat-1
host 202.100.1.101
object network pat-2
host 202.100.1.102
object network Inside-Network
subnet 10.1.1.0 255.255.255.0
object service telnet23
service tcp destination eq telnet
object service telnet3032
service tcp destination eq 3032
nat (Inside,Outside) source dynamic Inside-Network pat-1 destination static dst-1 dst-1 service telnet23 telnet23
nat (Inside,Outside) source dynamic Inside-Network pat-2 destination static dst-202 dst-202 service telnet3032 telnet3032object nat:nat是object的一个参数,实体为object,可以方便的被用于调用(如:ACL),只能改源或目
twice nat:object是nat的一个参数,可以添加自定义的object(或group),扩展性强,可以同时改源目
nat顺序
优先级一:
Twice NAT 敲入的顺序
Twice可以随意调整顺序
优先级二: Object NAT
静态转换优先于动态转换
如果类型相同,按照如下方式排序
1.地址范围
2.IP地址数字大小
4.Object名字排序
192.168.1.1/32 (static)
10.1.1.0/24 (static)
192.168.1.0/24 (static)
172.16.1.0/24 (dynamic) (object abc)
172.16.1.0/24 (dynamic) (object def)
192.168.1.0/24 (dynamic优先级三: Twice NAT
after-auto
更改排序
默认twice nat优先object nat,当在twice nat加after-auto参数,就会放在object nat之后
nat (Inside,Outside) after-auto source dynamic Inside-Network pat-1 destination static dst-1 dst-1 service telnet23 telnet23后敲的twice nat要排在前面,需要加 1
nat (Inside,Outside) 1 source dynamic Inside-Network pat-1 destination static dst-1 dst-1 service telnet23 telnet23亿速云「云服务器」,即开即用、新一代英特尔至强铂金CPU、三副本存储NVMe SSD云盘,价格低至29元/月。点击查看>>
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。